Thesis.
The next institutional unlock won’t be bridges that move bank assets onto public chains. It will be attestation‑mediated hedging portals that let regulated DLTs (e.g., Canton) rent public perps liquidity without exporting the underlying assets. The key insight is simple: private ledgers already run large, recurring money‑market flows; public perps already provide deep, on‑chain derivatives liquidity. The path of least resistance is not to commingle custody and compliance across those domains, but to connect them with verifiable facts—policy‑aware attestations—so that a repo or CP ticket done on a bank‑grade chain can be hedged on public venues while assets, cash, and counterparties remain fenced. Private DLT rails already clear large, recurring money‑market flows—e.g., Broadridge’s DLR processes over $1T of repo per month, while JPM’s Onyx intraday repo has handled $300B+ of transactions to date.
This is contrarian because most “RWA interoperability” talk still assumes moving tokens across a bridge or listing a bank asset as collateral on a DeFi venue. In practice, regulatory posture, privacy requirements, and operational risk push in the opposite direction. Institutions will hedge where liquidity is, but they will not move the securities. Attestation‑first portals square that circle.
Why bridges won’t carry the day (and why attestations will)
When people say “bring institutions on‑chain,” they often imagine turning a bank’s asset into an ERC‑20 and letting it roam the public mempool. That picture breaks on first contact with reality:
Policy & privacy. Money‑market desks, repo traders, and treasurers operate on rule‑bound workflows. Legal agreements encode who can see what, when. Many of those constraints (information barriers, client confidentiality, allocation rules) are incompatible with public broadcast.
Operational risk. Bridges add new custody domains and new failure modes (key management, relayers, oracles). If the use case is hedging, there is no reason to expose the asset to those risks.
Regulatory direction. Supervisors have been steady: they want interoperability with controls, not porous bridges that make enforcement ambiguous. That’s why “trust‑anchor” models and permissioned synchronization have traction: they preserve perimeters. Recent policy work emphasizes “interoperable networks with safeguards” rather than porous bridges—see MAS Project Guardian’s frameworks for tokenised fixed income and open networks.
Attestations solve the right problem. The hedge leg needs proof about a position (e.g., size, tenor, reference rate, settlement window), not the asset itself. If the Canton side can cryptographically attest to those facts—and the perps venue can accept them behind KYC/RFQ/dark‑pool gates—then both sides win:
Canton keeps assets, cash, and participant allowlists in‑bounds with sub‑transaction privacy: Canton provides sub‑transaction privacy and contract‑level authorization; participants see only what they’re entitled to, and applications synchronize without global broadcast.
The perps venue matches/clears the hedge where depth already exists, but only for admitted entities whose attestations validate.
Risk systems reconcile P&L with auditable receipts in both domains; nothing “leaks” that shouldn’t.
The attester can rely on sub‑transaction privacy and contract‑level authorization on Canton (facts only cross domains), which is exactly the security model institutions need. The point is not to make bank assets “DeFi‑native.” It’s to let bank‑native trades borrow DeFi’s liquidity through facts, not bridges.
Mechanism: how an attestation‑mediated hedge would actually work
Think in two rails: Asset Rail (regulated DLT) and Hedge Rail (public perps). The rails synchronize via Attestation Rail (facts, not funds).
1) Trade on the Asset Rail
A dealer and a client execute, say, a repo or CP issuance on a privacy‑preserving chain (e.g., Canton). The ledger enforces authorization and visibility: the repo terms (collateral, haircut, maturity) are known to parties of record; other participants see nothing beyond their entitlements. Settlement is atomic under the ledger’s rules; cash and securities reside with their respective custodians or trust models, not on a public chain.
Output: a canonical event record with sufficient detail to hedge (size, reference, timing) and sufficient constraint to preserve privacy. This mirrors production systems at scale today (see DLR and Onyx volumes above).
2) Produce / verify an Attestation
A bank‑operated or neutral service derives an attestation from the trade (e.g., “Party A holds a short‑duration rate exposure of X notionals against index Y over window T; Party B is authorized to hedge on A’s behalf”). The attestation includes:
Data minimization (only what the hedge venue needs).
Policy proof (the client and agent are allowlisted; AML checks; concentration limits).
Revocation hooks (if the underlying is amended/closed, the attestation state changes).
Attestations are signed, optionally ZK‑wrapped, and time‑bounded. Think “composable compliance object,” not a moving token.
3) Submit to a KYC‑gated hedge module on the perps venue
On the perps side, you do not throw this into a public order book. You route to a permissioned RFQ / dark‑pool or segmented liquidity pool where only admitted participants can quote and cross. The venue checks:
The attestation’s cryptographic validity and current status.
Participant identity and entitlements against its own KYC/AML store.
Exposure limits (venue‑side risk).
Quotes come back (e.g., receive/ pay fixed via basis swaps; short perps basket; structured delta hedge). The client (or agent) lifts a quote; the hedge position is opened on the perps ledger. No assets are bridged; only derivatives positions are created. Liquidity and execution quality on perps DEXs are already institutional scale: CoinGecko estimates $898B in DEX‑perps volume in Q2’25 (~$10B/day), and DefiLlama shows billions more across chains weekly.
4) Reconcile and settle P&L
Marking, funding, and P&L stay native to the hedge venue. The attestation ID travels with fills. Post‑trade, receipts (fills, fees, P&L) are returned to the attestation service for reconciliation:
Asset‑rail records reflect that the exposure is hedged.
Hedge‑rail records reflect why a given admitted user was allowed to trade.
Auditors can prove consistency without learning confidential details.
5) Lifecycle events
If the repo rolls, is amended, or terminates, the attestation updates. If it is revoked, new hedges cannot be opened and risk systems prompt unwind. Margin calls on the perps side are funded from admitted accounts (custody bank ↔ venue accounts), not from the regulated DLT itself.
Result: The bank never exported the asset, never exposed client data to a public mempool, and never accepted new custody domains; yet they accessed the market with the most elasticity to lay off risk. The perps venue never touched a bank asset and never took on enforcement duties; yet it captured institutional flow it otherwise wouldn’t see.
Evidence stack: why this is the right wedge now
1) The private‑ledger side is already “real.”
Bank‑grade ledgers that provide sub‑transaction privacy and contract‑level authorization are not hypothetical. They clear large, repeated money‑market flows today. The order of magnitude matters: tens of billions per day in repo and related settlement moving through private DLT rails is not a science experiment—it is production. That scale means the exposure exists and is clock‑like: perfect for standardized hedges. (Broadridge DLR: >$1T/month; JPM Onyx intraday repo: $300B+ cumulative.)
2) The public‑perps side is already “deep.”
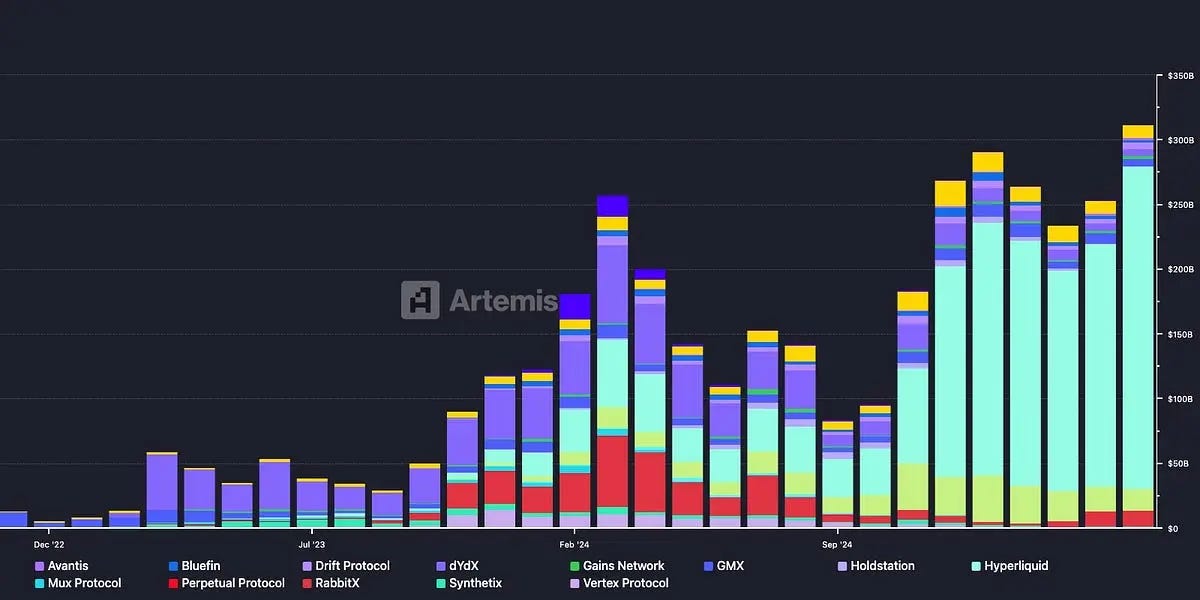
On‑chain perps are active and institution‑scale. Artemis’ market‑share work shows Hyperliquid commanding “over 75%” of decentralized perps volume in early 2025, based on their protocol share analysis. In terms of flow magnitude, Artemis’ weekly fundamentals note recorded ~$3.5B of daily DEX‑perps volume on March 2, 2025 (with ~$6.5B spot‑DEX that day), underscoring that weekly throughput reliably sits in the multi‑tens‑of‑billions. That depth—plus its institution‑facing features like RFQ desks and curated market‑maker programs—makes it the natural first integration point for KYC‑gated flow. More important than raw volume, their order‑book mechanics, funding curves, and index quality now support institutional‑grade hedging (basis, curve hedges, multi‑asset baskets). The liquidity is there today; the blocker is compliant access, not depth.
3) Policy direction supports “interoperability with controls.”
Global regulators have consistently nudged toward interoperable networks that preserve controls (trust anchors, whitelists, governance frameworks) rather than naive bridges. Read the tea leaves: sandbox pilots emphasize permissioned synchronization across domains and policy‑aware gateways—i.e., exactly the attestation path. The more money‑market and fixed‑income use cases appear in those sandboxes, the more pressure there is to provide standardized, attestable facts across ledgers.
4) Builders on both sides are converging.
On the bank side, tokenization stacks and workflow DLTs keep investing in privacy, policy, and DAML‑like contract languages. On the public side, the leading perps ecosystems are actively building RFQ desks, dark‑pool‑style matching, and institutional KYC paths. The organizational will exists in both camps; an attestation rail is the minimum viable connection.
Objections (the strongest ones) & rebuttals
Objection 1: “Banks won’t touch public perps.”
Banks won’t touch permissionless perps as retail users do, and they won’t broadcast orders in the clear. This design explicitly avoids that. KYC‑gated, RFQ/dark‑pool modules and attested entitlements mean the bank’s compliance domain is not pierced. From the bank’s perspective, the hedge venue is just another admitted broker‑dealer‑like counterparty with appropriate agreements, surveillance, and record‑keeping—plus the auditable trail of an attestation service.
Objection 2: “Attestations are soft; bridges are hard assets.”
That’s the point. Attestations can be cryptographically bound to trade events, time‑boxed, and revocable—a design explicitly supported by Canton’s privacy/authorization model. You don’t need to move the asset to hedge its risk. Attestations can be cryptographically bound to trade events, include policy proofs (allowlists, AML checks), and be revoked if the underlying changes. They can be ZK‑minimized to leak no more than necessary and referentially consistent so audits line up end‑to‑end. Bridges move custody risk; attestations move facts.
Objection 3: “What if the perps venue front‑runs or leaks?”
The flow goes to non‑displayed / segmented liquidity with narrow admission and post‑trade transparency. The venue’s economic moat is passing institutional audits and winning top‑tier MM support—not retail order‑flow skimming. As with dark pools in TradFi, the commercial incentives align with protecting client flow once the pipeline exists.
Objection 4: “Why not keep everything on private ledgers?”
Because liquidity begets liquidity. Private ledgers excel at workflow, settlement finality under known legal wrappers, and privacy. They do not excel at broad, 24/7 derivatives liquidity across thousands of instruments. Public perps do. The attestation approach lets each domain do what it’s best at without merging trust boundaries.
Practical implications (for investors, builders, and institutions)
If you’re an investor
Basis compression trade. Once attested hedging turns on, expect perps‑cash basis for benchmark exposures to compress toward repo‑implied levels, especially around month‑end and quarter‑end where bank flows are thickest. Watch funding rates vs. money‑market prints after the first integrations.
Pick the rails. Allocate to perps ecosystems that deliver KYC/RFQ/dark‑pool first—and to middleware that can issue/verify attestations (identity, policy proofs, ZK attestations, revocation registries).
Short weak bridges / long trust anchors. The more regulated flows arrive without bridges, the worse the outlook for “generic bridge tokens” and the better for trust‑anchor models (custodians, identity providers, compliant oracles).
If you’re a builder (perps venue)
Ship the compliance shell. Implement an admitted‑participants segment with RFQ, non‑displayed books, and per‑account entitlements. Your edge is interoperating with attestation formats, not inventing new ones.
Quote the right products. Money‑market desks want index‑hedge clarity (rates, basis baskets, short‑tenor curves), low slippage, and known funding mechanics. Win that, and secondary products follow.
Operationalize proofs. Make attestation verification first‑class: caching, revocation checks, and deterministic policy outcomes. If a bank’s attestation flips state, your matching engine’s reactions must be crisp.
If you’re a bank or asset manager
Outsource what’s not core. Don’t try to be a public‑chain custodian. Keep assets and clients in your trust domain; export facts for hedging.
Demand reversibility and auditability. Your interoperability contract should specify revocation semantics, attestation lineage, and survivable logs. “We can prove what happened” is the only way this scales internally.
Start small, scale deterministic. Pilot with narrow tenors/instruments (e.g., index‑linked short perps, basis baskets), then expand. You want a predictable playbook your control functions can bless.
What to watch in the next 3–9 months (explicit catalysts)
An attestation‑format announcement co‑signed by a regulated DLT provider, one or two custodians/IDPs, and a major perps venue. Even a “sandbox spec” is enough—what matters is a public handshake that a verifiable fact can cross domains.
KYC/RFQ/dark‑pool go‑live on one marquee perps chain (e.g., Hyperliquid, the current leader by DEX‑perps volume) with audit artifacts (policy docs, penetration tests, participant admission criteria). This is the “door” institutions need; without it, nothing else matters.
First production‑like tickets: small‑notional hedges where a money‑market exposure on a bank ledger is hedged on a public perps venue under attestation. Look for press language like “no asset movement; attested connectivity; revocation‑capable.”
Custody APIs exposing policy‑aware hooks (allowlist checks, cash sweep to fund margin, legal hold events). When custodians publish developer docs that explicitly mention attested trading access, the game moves.
Regulator commentary in sandbox reports highlighting interoperability with controls and attestation‑style proofs. Even cautious prose is a green light.
Falsifiers: a high‑profile incident where an institution tried “tokenize‑and‑bridge” and suffered a compromise; or an explicit regulatory statement that forbids any connectivity to public venues even via admitted segments. Either would delay (not kill) the thesis.
How this plays out (timeline & end‑state)
Phase 1 (0–6 months): Plumbing appears. An attestation standard emerges; one or two perps venues light up admitted segments; one or two custody providers expose the right APIs. Early pilots hedge index‑like exposures (rates, BTC/ETH baskets) with narrow participant sets. Most observers miss it because notionals are small.
Phase 2 (6–18 months): Flow grows. Money‑market desks routinize the playbook: attest → quote → hedge → reconcile. The venues refine margin, funding, and basket construction for institutional taste. Basis begins to tighten structurally around roll dates. Middleware (issuers of attestations, ZK policy engines, identity anchors) starts to look like an investable category.
Phase 3 (18–36 months): Multiplication. With confidence in the pipe, product breadth expands (more indices, tenor ladders, vol overlays). The “attestation rail” generalizes beyond repo/CP into FX hedges, duration overlays for tokenized funds, and structured exposures for treasuries. At this point the debate is over: flows live on private ledgers; hedges live on public ones; attestations knit them together.
Conclusion
The crypto community has been asking “When institutions?” for years. The answer is hiding in plain sight: they’re already here—but their assets live on private, policy‑preserving ledgers that match their legal and operational constraints. Meanwhile, the largest, most elastic pool of on‑chain risk transfer is in public perps. The winning play is not to drag bank assets across a bridge and pray; it’s to export verifiable facts—attestations—so those exposures can rent liquidity exactly where it’s deepest.
This setup is asymmetric. The private‑ledger side does not need to change its custody model. The perps side does not need to take on new enforcement roles. Both only need to accept the minimal, auditable connection: “Here is an admitted participant with a valid, revocation‑capable attestation; let them trade in the admitted segment.” Once that door exists, the first hedges will look small and boring. Then, slowly, the basis tightens, the product set expands, and a new class of buyers and sellers quietly seats itself in public order books.
That’s the Multicoin‑style bet: be early to the rails (KYC/RFQ/dark‑pool + attestations), ignore the noise around generic bridges, and position for the day money‑market desks start treating an on‑chain perps venue like just another place to hedge—while their assets never leave home.
DISCLAIMER
The views and information presented here are offered by me in an individual capacity and do not represent any firm, fund, or other organization. All content is provided “as is,” with no warranties—express or implied—regarding accuracy, completeness, timeliness, or fitness for any purpose. Nothing in this material constitutes—or should be interpreted as—financial, legal, tax, or investment advice, nor does anything herein constitute a solicitation, offer, or recommendation to buy, sell, or hold any security, digital asset, or other instrument.
You alone are responsible for evaluating the merits and risks associated with any action you take based on the information provided. I accept no liability for any loss, damage, or harm—direct or consequential—that may arise from reliance on this content or from any investment decisions you make. Information is impersonal, not tailored to your circumstances, and may become outdated without notice.
By reading or otherwise using this material, you acknowledge and agree to these terms



